Integrate Agent with Secrets Manager Using IAM Instance Profile¶
Alation Cloud Service Applies to Alation Cloud Service instances of Alation
Available on the Deluxe, Enterprise, and Enterprise+ plans only
Use the information in this topic to configure an Alation Agent installed on an Amazon EC2 instance to read secrets from AWS Secrets Manager by attaching an IAM role to the Agent’s IAM instance profile. With the Alation Agent, AWS Secrets Manager, and your on-premise data source all running within your Virtual Private Cloud (VPC), your data source credentials will never leave your VPC, and they are not stored in Alation or the Alation Agent.
Step 2: Create an AWS IAM Role for the Alation Agent’s EC2 Instance
Step 3: Install the Authentication Service Add-on on the Alation Agent
Note
To see other options for integrating with AWS Secrets Manager, see Integrate with AWS Secrets Manager.
Prerequisites¶
You must be on Alation Cloud Service version 2024.1.4 or later.
Your Alation Agent must be installed on an Amazon EC2 instance.
You must be using Alation Agent version 1.7.2.4360 or later.
You must install Authentication Service Add-on version 5.14.0.1882 or later on the Alation Agent.
You must have a supporting OCF connector installed on the Agent. To find out if a specific connector supports this feature, see the documentation for the specific connector in the Open Connector Framework (OCF) Overview section.
Note
You can use the Native Data Sources API to migrate a data source from an OCF connector that’s not on an Alation Agent to an OCF connector that is on an Alation Agent.
For EC2 machines using IMDS v2, ensure that the hop limit has been increased to 2 as recommended by AWS.
You must have the Server Admin role to set up the integration in Alation.
Step 1: Create a Security Policy to Access Secrets Manager¶
This step is performed in the AWS IAM console
For the AWS Secrets Manager integration, you’ll need an AWS IAM policy granting access to AWS Secrets Manager. Here and below, a substitute name read_secrets_policy is used to refer to this policy.
If you haven’t established a read_secrets_policy yet, create one:
Log in to the AWS IAM management console.
From the left-hand menu, under Access management, select Policies.
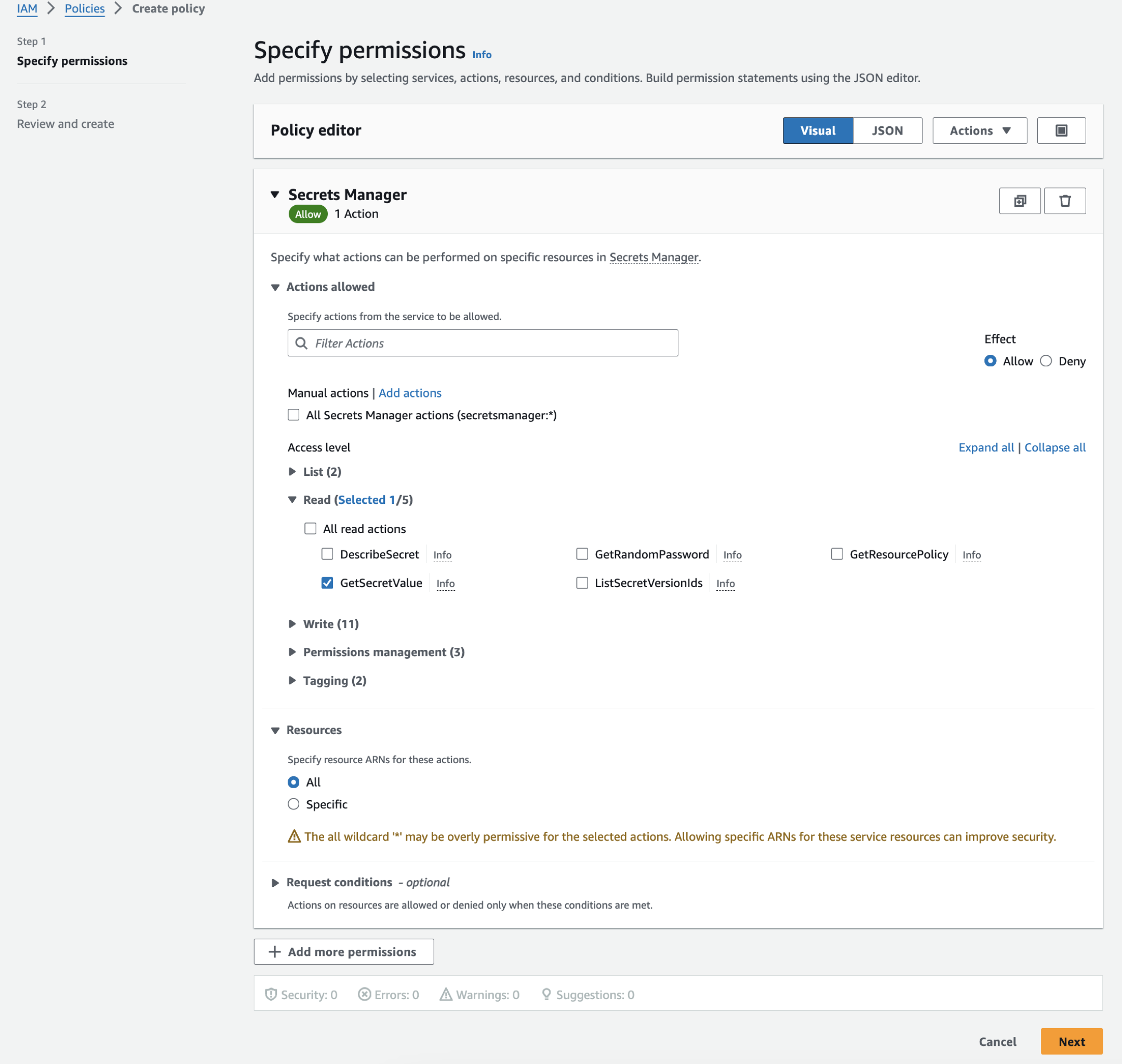
Click Create policy. The policy editor will open.
Under Select a service, type secrets in the search bar and select Secrets Manager. This will display actions relevant to the service.
Under Actions allowed, expand the Read list and select the checkbox for the action GetSecretValue.
Under Resources, select All.
Note
You can restrict the permissions by providing access to specific resources only:
Instead of All, select Specific.
Click Add ARNs to specify the resources by entering the resource’s region, ARN (Amazon Resource Name), and secret.
You can adjust the resource permissions anytime by editing this policy.
Click Next. The Review and create screen will open.
Under Policy details, in the Policy name field, provide a meaningful name.
Review the details, and click Create policy to create the policy. It will be added to the list of policies under your AWS account. Your policy JSON will look similar to the following:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": "secretsmanager:GetSecretValue", "Resource": "*" } ] }
Note
An Alation Agent deployed on an AWS EC2 machine can retrieve secrets from a separate AWS account (cross-account access). For example, the Alation Agent machine could be deployed in Account 1, and the AWS Secrets Manager could be deployed in Account 2. This requires additional setup as described in AWS documentation here: Access AWS Secrets Manager secrets from a different account.
Step 2: Create an AWS IAM Role for the Alation Agent’s EC2 Instance¶
This step is performed in the AWS IAM console
Now that you’ve created an IAM policy for accessing AWS Secrets Manager, you need to create an AWS IAM role and attach the policy to it. Here and below, a substitute name read_secrets_role is used to refer to this role.
If you haven’t established a read_secrets_role yet, create one:
From the left-hand menu, under Access management, select Roles.
Click Create role. The role editor will open.
Leave AWS service as the Trusted entity type (default) and select EC2 as the Use case.
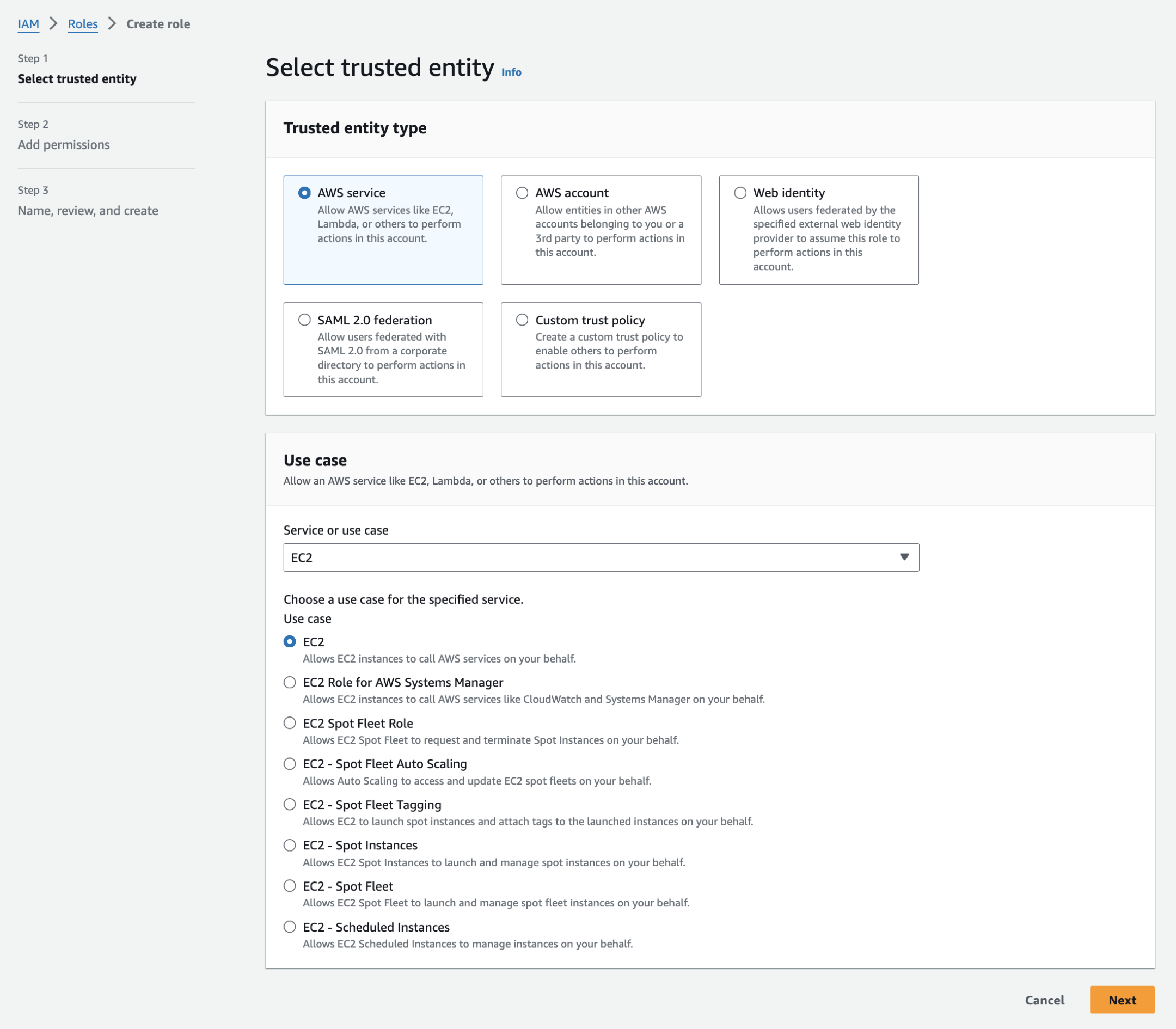
Click Next. The Add permissions screen will open.
Under Permissions policies, search for the policy you created to allow reading secrets from Secrets Manager. When found, select the checkbox of this policy in the policies table.
Click Next. The Name, review, and create screen will open.
In the Role name field, provide a meaningful name. We’ll use
read_secrets_roleas example.In the Description field, provide a description.
Review the role information and click Create role to create the role. It will be added to the list of roles under your AWS account. This role will be assumed by the instance profile to access Secrets Manager from Alation.
Attach this role to the EC2 instance where the Alation Agent is running: navigate to EC2, open the properties of the instance, and select Action > Security > Modify IAM Role > Select IAM Role > Update IAM Role. For more information, refer to Attach an IAM role to an instance in AWS documentation.
Step 3: Install the Authentication Service Add-on on the Alation Agent¶
This step is performed in Alation or on the Alation Agent machine
To enable the Alation Agent to communicate with AWS Secrets Manager, you must install the Authentication Service add-on on the Agent.
See Install the Authentication Service Add-on for help installing the Authentication Service add-on.
Step 4: Create an Authentication Profile¶
This step is performed in Alation
To create an authentication profile for the Secrets Manager integration:
Log in to your Alation instance as a Server Admin.
Click the Admin Settings gear icon on top right to open the Admin Settings page.
Click Authentication to open the Authentication tab. Locate the section Authentication Configuration Methods for External Systems.
Next to See configurations for, click the drop-down menu and select the relevant Alation Agent.
Click Add Configuration, and then select AWS Secrets Manager as the method type. The Authentication Configuration Method page will open in a new browser tab.
In Config Name, enter a unique name for the configuration. Save it for future reference when configuring the data source.
Under Region, select the appropriate AWS region for the Secrets Manager service (the region under which your secrets are stored).
Under Authentication Type, select IAM Instance Profile.
Click Save. Alation attempts to create a connection, and if the connection is successful, the configuration is saved.
Now, you can use your integration with an OCF connector. See next: Configure Authentication with AWS Secrets Manager for a Data Source.
